
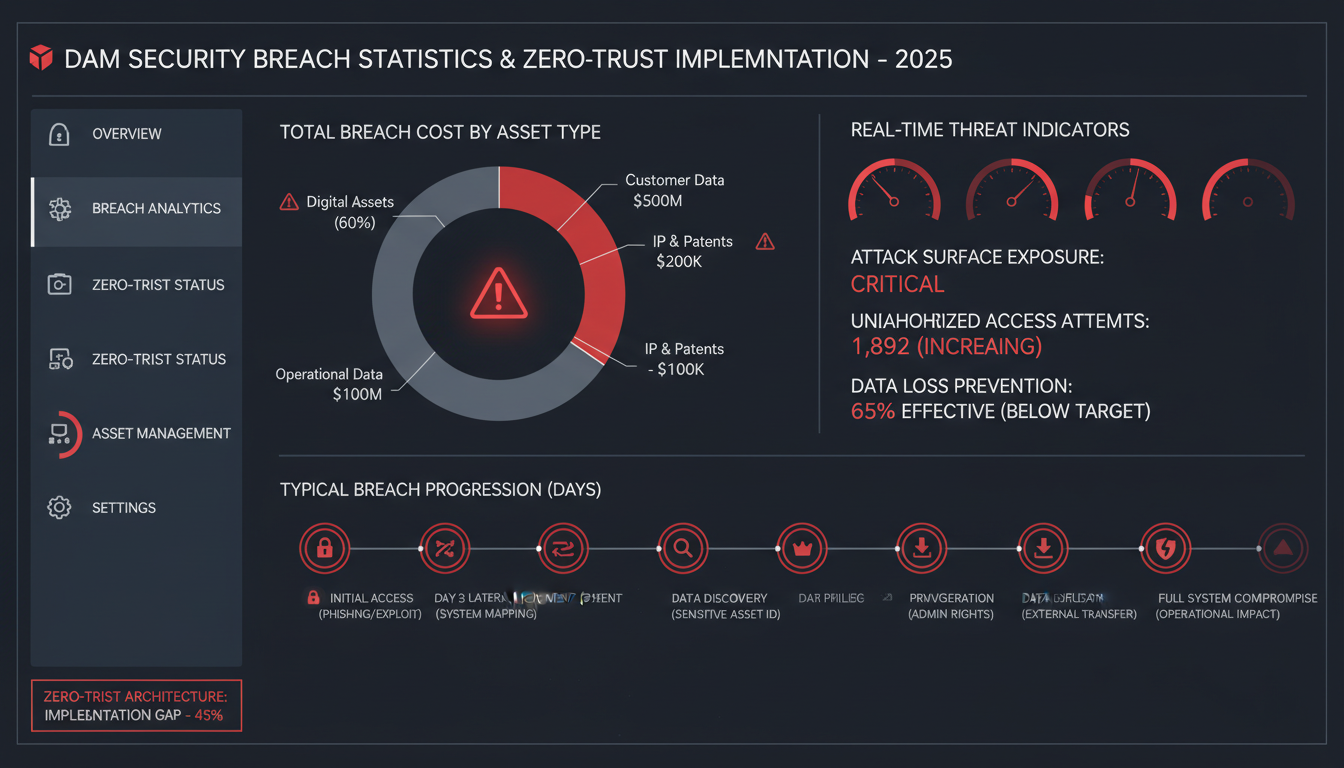
Digital asset breaches cost enterprises an average of $4.88 million in 2024, with stolen creative files, brand assets, and proprietary content driving litigation costs through the roof. Your DAM system stores millions of dollars worth of digital intellectual property—yet most organizations still rely on perimeter-based security that fails the moment an attacker gets inside.
The problem is clear: Traditional DAM security assumes trust once users authenticate. One compromised credential can expose your entire asset library.
Enter dam security zero-trust architecture. This approach treats every access request as potentially hostile, regardless of user location or previous authentication. Instead of "trust but verify," zero-trust operates on "never trust, always verify."
For IT security managers and CISOs managing enterprise DAM deployments, 2025 demands a fundamental shift. You can't afford to treat digital assets like traditional files anymore. A leaked product launch video or stolen brand guidelines can derail entire campaigns.
Here's what you'll learn in this guide:
• Asset-level encryption that protects files even when downloaded • Micro-segmentation strategies that isolate high-value creative assets
• Dynamic access policies that adapt to user behavior and context • Secure delivery methods that prevent unauthorized sharing • Implementation roadmaps that won't disrupt current workflows
Zero-trust architecture transforms your DAM from a file repository into a secure digital vault. Every asset gets encrypted individually. Every access request gets evaluated in real-time. Every download creates an audit trail.
The enterprises implementing these strategies now will maintain competitive advantage while others deal with breach recovery costs and reputation damage. Let's examine exactly how to build bulletproof DAM security.
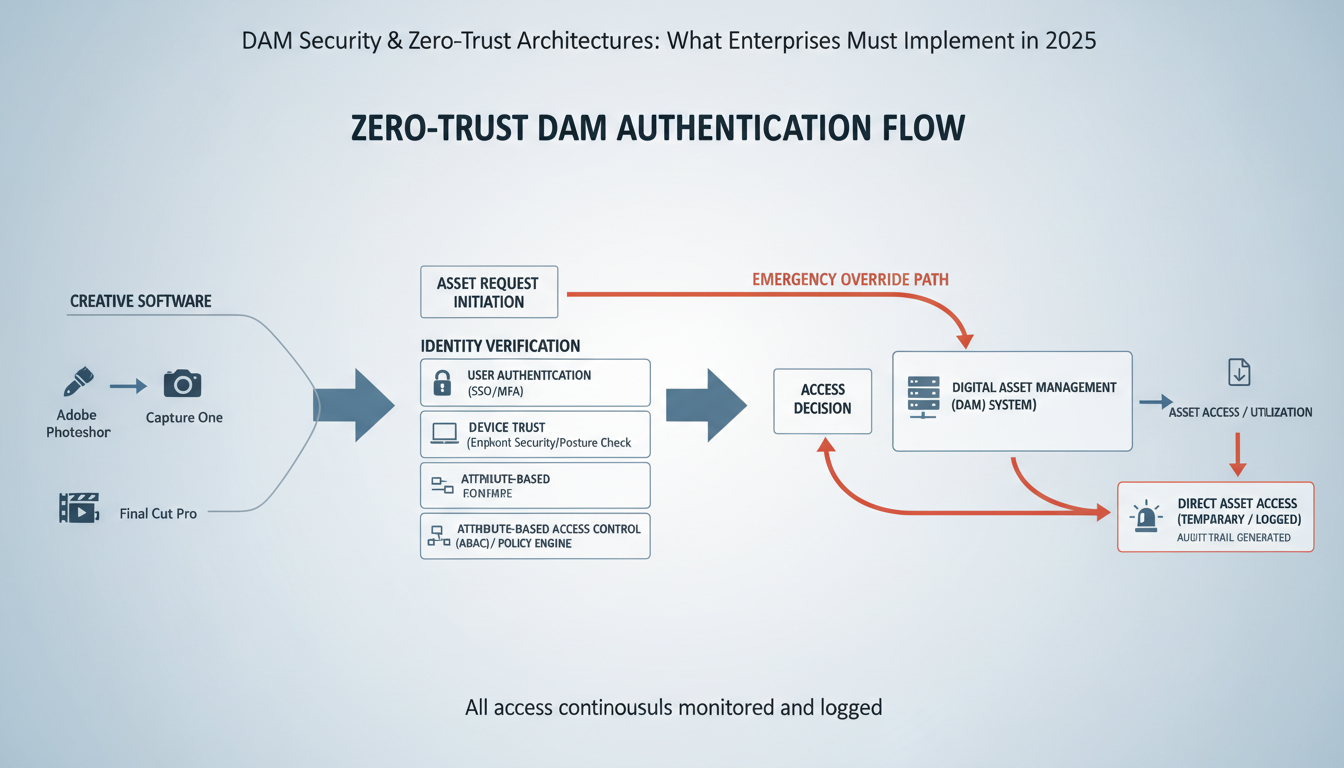
Traditional security models assume everything inside the corporate network can be trusted. That assumption fails spectacularly when applied to digital assets. Dam security zero-trust operates on a fundamentally different principle: "Never trust, always verify" – for every asset, every user, every access request.
Network zero-trust secures infrastructure. DAM zero-trust secures content itself. When a marketing manager downloads 47 brand logos from your DAM, zero-trust architecture validates their identity, confirms their device meets security standards, and grants access only to specific assets they need for their campaign.
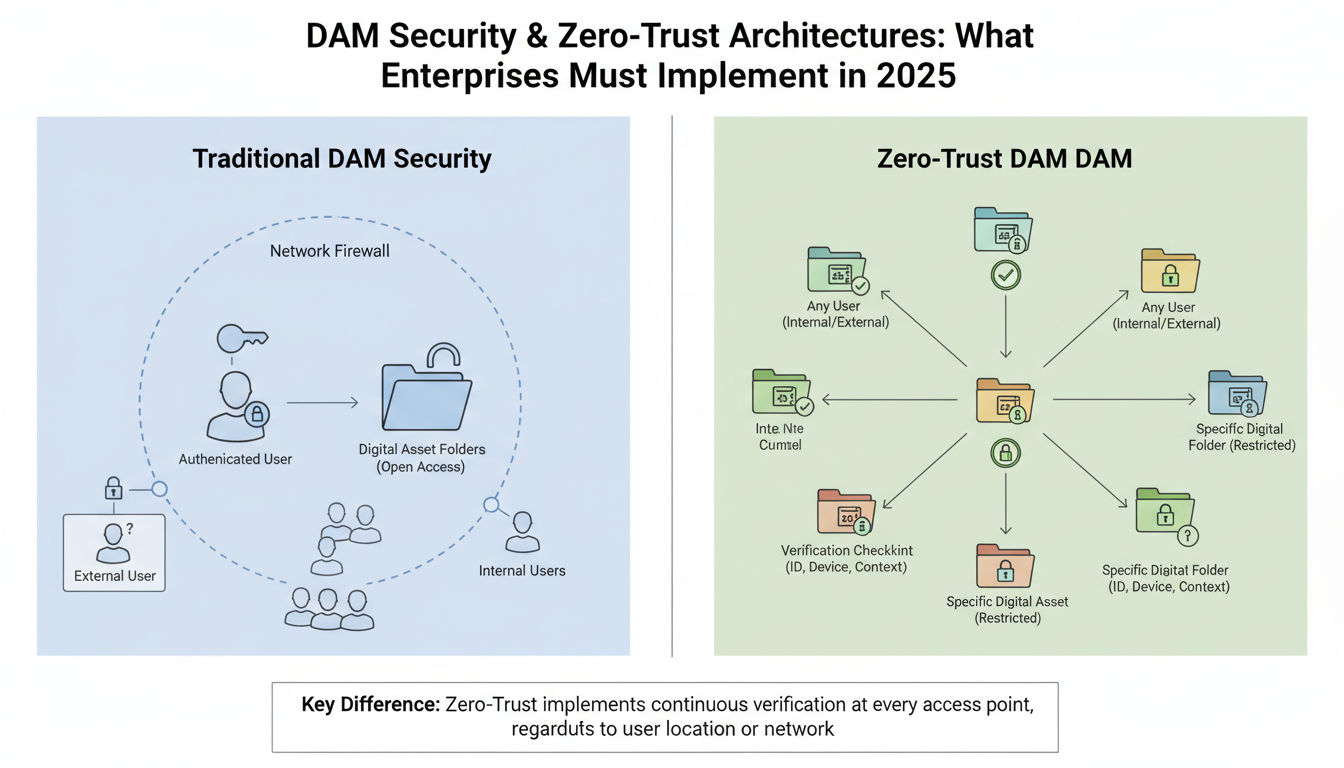
Identity verification goes beyond single sign-on. Every request triggers real-time validation: Is this Sarah from Marketing? Is she accessing assets during normal work hours? Has her role changed since yesterday?
Device validation checks endpoint security status before allowing downloads. That contractor's laptop with outdated antivirus? Blocked from accessing your $2 million product photography collection.
Asset-level permissions create granular control. Your creative director gets full resolution files. External agencies receive watermarked previews only.
Here's why traditional DAM fails: A phished marketing coordinator's credentials grant access to thousands of assets. Attackers download everything – product roadmaps, unreleased campaigns, customer data embedded in design files. Zero-trust prevents this lateral movement by validating every single asset request, even from authenticated users.
Modern access policies should assume breach has already occurred. When your DAM requires fresh authentication for sensitive assets, implements asset encryption at rest and in transit, and logs every download with behavioral analysis, you've built defense in depth.
Secure delivery becomes automatic when zero-trust principles govern your DAM. Each asset carries its own access rules, expiration dates, and usage restrictions – regardless of where it travels.
Most enterprise DAM implementations contain three fundamental security flaws that zero-trust architecture directly addresses. Understanding these vulnerabilities is essential before implementing dam security zero-trust protocols.
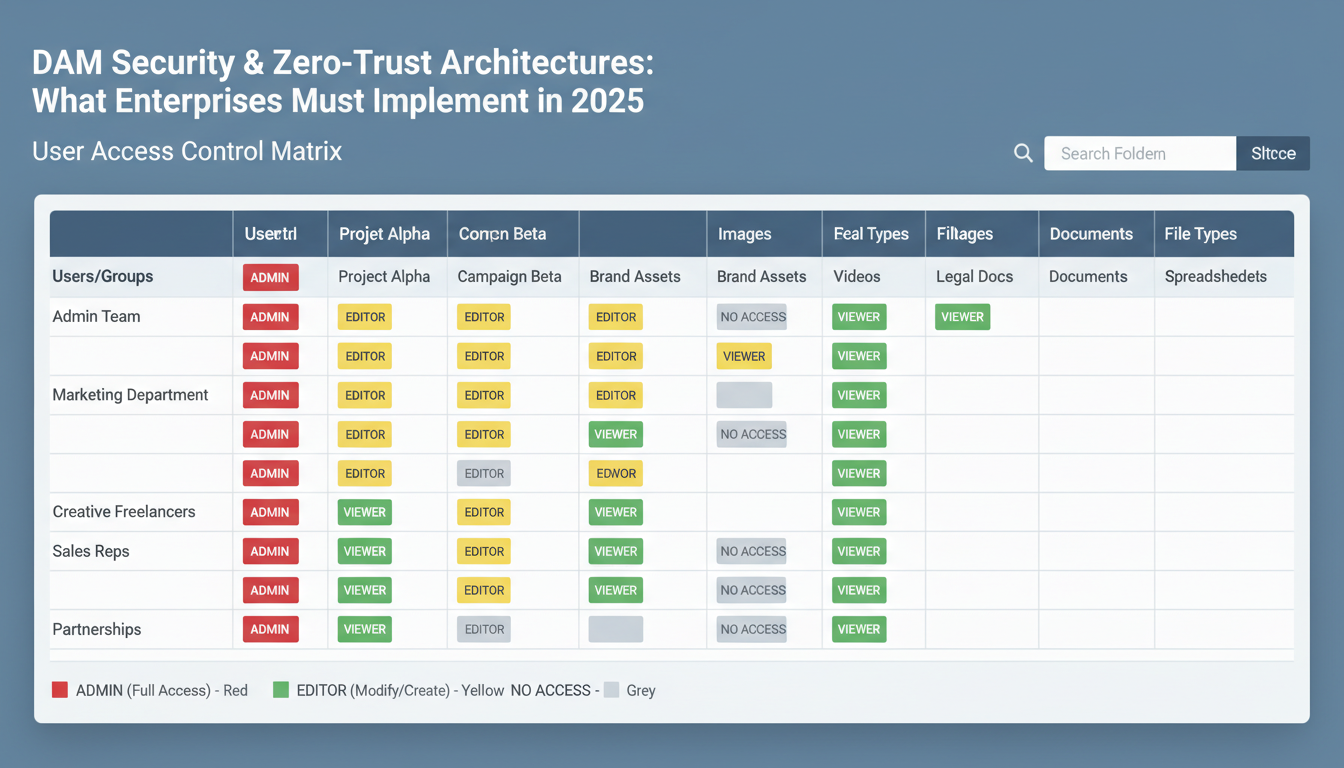
Shared access credentials plague 67% of DAM implementations according to 2024 security audits. Marketing teams routinely share "creative@company.com" logins across departments. This creates audit nightmares. When a breach occurs, you can't identify who accessed what assets or when.
Zero-trust architecture eliminates this by requiring individual authentication for every user and device. Each access request gets verified independently, regardless of previous sessions.
Many DAM systems store high-value creative assets without encryption. Brand guidelines, unreleased product images, and marketing campaigns sit exposed in plain text databases. During transmission, these files often travel unprotected across networks.
Asset encryption must occur both at rest and in transit. Modern zero-trust systems encrypt every file individually with unique keys.
The average DAM user has access to 11 million files. That's excessive. A junior designer doesn't need access to executive presentations or financial documents stored alongside creative assets.
A major fashion retailer suffered a DAM breach in late 2023 when attackers accessed 2.3TB of unreleased seasonal designs through shared credentials. The breach cost $847 per compromised digital asset – totaling $1.9 million in damages from leaked designs, legal fees, and competitive disadvantage.
Secure delivery protocols with individual user authentication could have prevented this breach entirely. The retailer has since implemented comprehensive access policies requiring multi-factor authentication for every DAM session.
Implementing dam security zero-trust requires sophisticated encryption that goes far beyond basic file protection. AES-256 encryption must be applied at the individual asset level, not just bulk storage containers. This means each video, image, and document gets its own encryption key—a resource-intensive approach that pays dividends in breach scenarios.
The performance trade-off is real but manageable. Proper AES-256 implementation adds 12-15ms latency per asset request. For a 500MB video file, encryption preserves all metadata while maintaining playback quality through streaming decryption. The key is processing encryption server-side before delivery, not during user interaction.
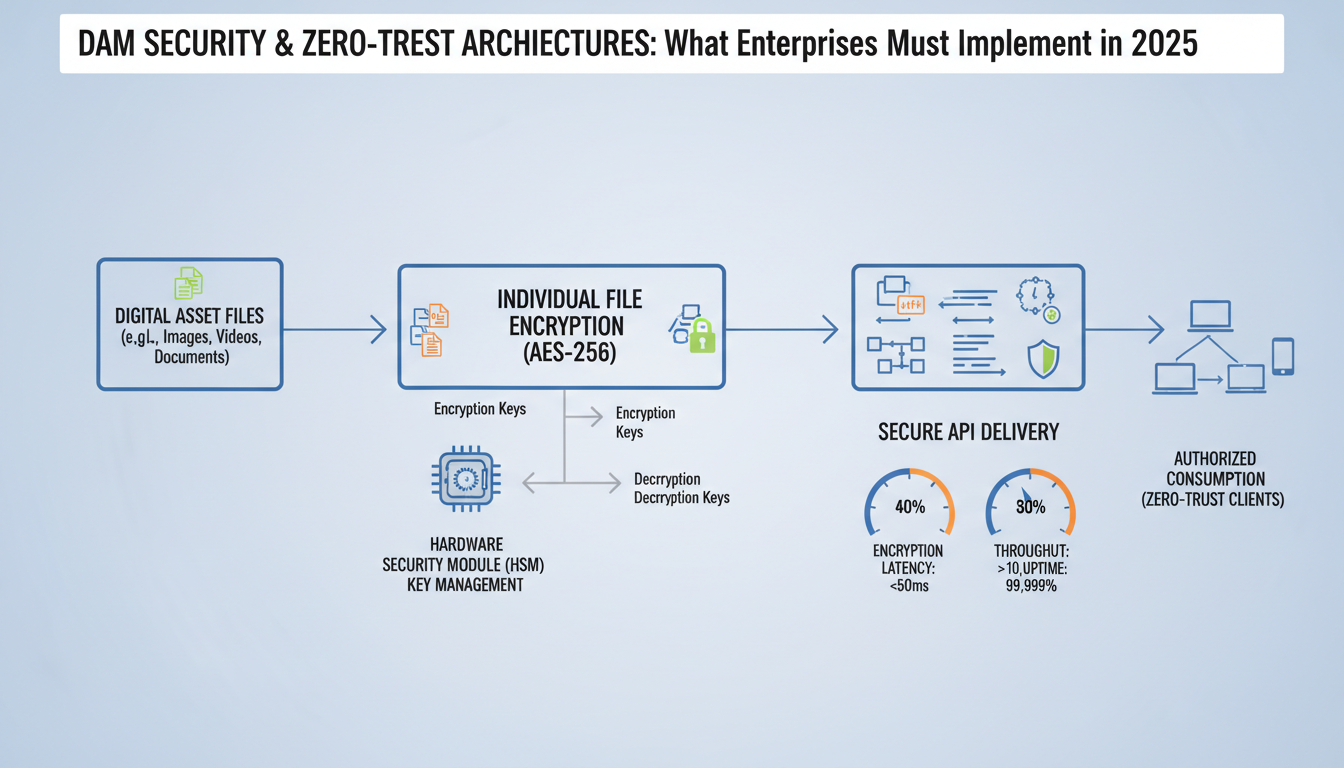
Hardware Security Modules (HSMs) must handle your key rotation strategy. Rotate encryption keys every 90 days maximum—weekly for high-value assets. This creates operational complexity but eliminates the "golden key" vulnerability where one compromised key exposes your entire asset library.
Zero-trust architecture demands encryption across three states:
The biggest implementation hurdle isn't technical—it's workflow disruption. Your existing DAM APIs need encryption/decryption middleware that doesn't break current integrations. Adobe Creative Cloud connections, content delivery networks, and automated publishing workflows must authenticate and decrypt seamlessly.
Smart asset encryption strategies use tiered approaches. Public marketing images get standard encryption, while proprietary design files and unreleased content receive enhanced protection with biometric access policies. This balances security requirements with operational efficiency.
Secure delivery through encrypted CDN endpoints ensures assets remain protected even during high-volume distribution campaigns.
Moving beyond traditional role-based access control (RBAC), zero-trust architecture demands attribute-based access control (ABAC) that evaluates multiple variables before granting asset access. While RBAC assigns permissions based on job titles, ABAC creates dynamic access policies that consider user attributes, environmental factors, and real-time risk assessment.
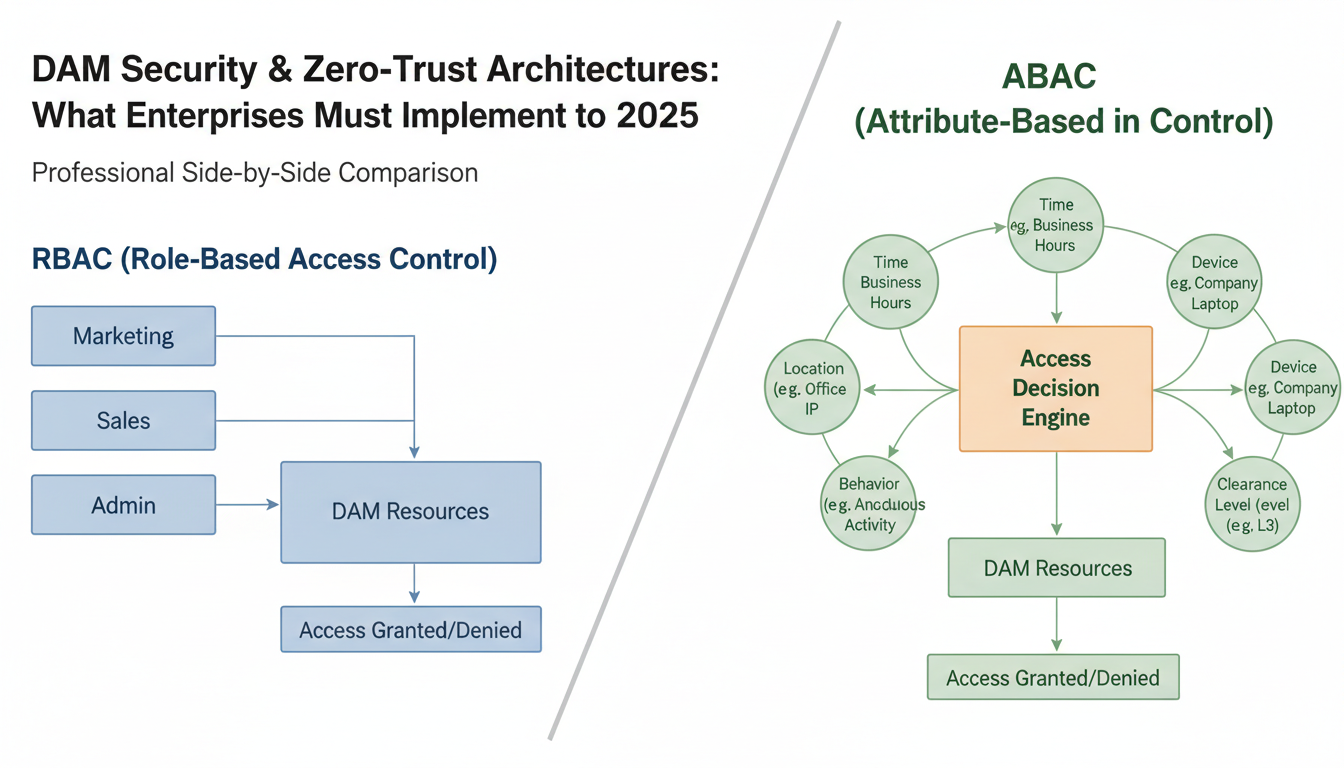
Enterprise DAM systems need granular access policies that adapt to context:
Time-based restrictions: Marketing teams access campaign assets only during business hours (9 AM - 6 PM EST), while emergency responders get 24/7 access to crisis communication materials.
Location-based controls: Legal documents remain accessible only from corporate networks or approved countries, preventing accidental GDPR violations when employees travel.
Device-type limitations: High-resolution product images download to managed corporate devices, while personal devices receive watermarked previews only.
Modern dam security zero-trust systems monitor user patterns continuously. When a designer typically accesses 50 assets daily suddenly downloads 500 files, the system triggers additional authentication. Integration with Azure AD, Okta, or Ping Identity enables seamless policy enforcement across your entire tech stack.
Track these metrics weekly:
Secure delivery becomes automatic when policies trigger appropriate encryption levels based on content sensitivity and user clearance. A financial report gets AES-256 encryption, while a company logo uses standard SSL transport.
This approach transforms static permissions into intelligent gatekeepers that protect your digital assets without hindering productivity.
Secure delivery forms the final critical layer where dam security zero-trust principles meet end-user access. TLS 1.3 implementation across all asset delivery endpoints isn't optional—it's mandatory for enterprise-grade protection. Unlike TLS 1.2, version 1.3 eliminates vulnerable cipher suites and reduces handshake latency by 50%.
CDN integration demands careful security configuration. Cloudflare's zero-trust architecture supports token-based asset access with custom headers, while AWS CloudFront enables signed URLs with IP restrictions. Both platforms now offer real-time threat detection that blocks suspicious download patterns within 200 milliseconds.
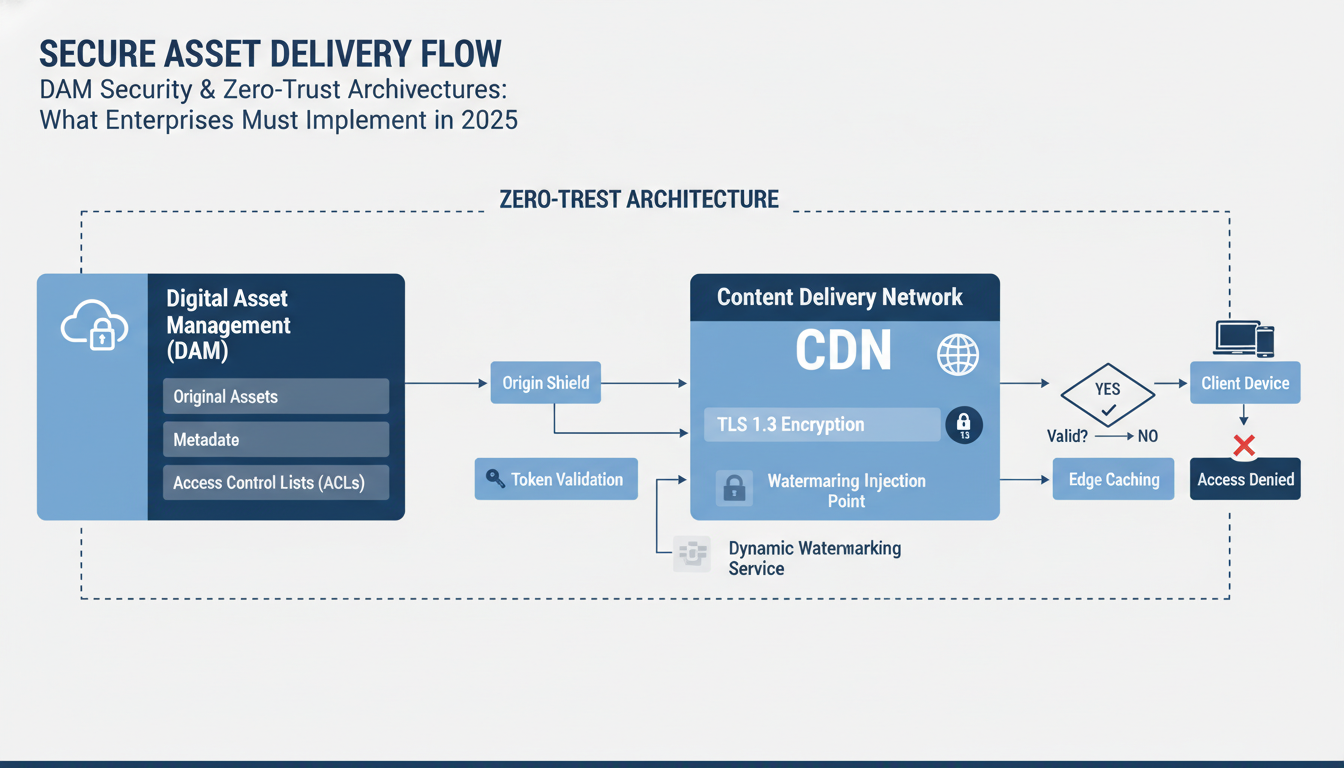
Asset encryption must extend to the delivery point. Dynamic watermarking injects user-specific identifiers during asset retrieval, not storage. Microsoft's PlayReady DRM integrates seamlessly with most DAM platforms, applying rights management policies that expire based on access policies rather than fixed timeframes.
API security requires OAuth 2.0 with PKCE (Proof Key for Code Exchange) for mobile applications. Standard OAuth flows expose authorization codes to interception, but PKCE generates dynamic code verifiers that change per session. Implement 15-minute token expiration for high-value assets.
Mobile apps present unique challenges. Certificate pinning prevents man-in-the-middle attacks, but requires careful update management. Pinterest's mobile team discovered that hardcoded certificates caused 23% of users to lose access during certificate rotation.
Implement progressive asset loading for mobile delivery. Load low-resolution previews first, then fetch full assets based on user interaction. This approach reduces bandwidth consumption by 60% while maintaining security through selective delivery.
Zero-trust architecture demands that every asset request undergoes fresh validation, regardless of previous authentication. Cache security tokens locally for performance, but validate against your DAM's policy engine before each delivery.
Traditional username-password combinations can't support dam security zero-trust requirements. Enterprise DAM systems need authentication methods that verify identity continuously, not just at login.
FIDO2 security keys eliminate phishing attacks entirely—something SMS codes can't achieve. YubiKey deployments across Fortune 500 companies show 99.9% attack prevention rates. Biometric authentication using Windows Hello or Touch ID creates device-specific access patterns that zero-trust architecture can track.
Hardware tokens generate cryptographic proofs that malicious actors cannot replicate remotely. When your marketing team accesses 50GB of video assets from different locations, certificate-based authentication ensures each device maintains verified credentials.
Static login verification fails in modern threat environments. Access policies must evaluate user behavior throughout each session. If someone typically downloads 10 assets daily but suddenly attempts 500 downloads, the system should trigger additional verification.

Risk scoring algorithms analyze 15+ factors simultaneously: device fingerprint, geographic location, access patterns, file types requested, and download volumes. Microsoft's Conditional Access uses similar scoring to block 99% of identity attacks.
Contractors and agency partners create the biggest asset encryption challenges. MDM integration ensures external devices meet security baselines before accessing sensitive brand assets.
Apple Business Manager and Microsoft Intune can enforce encryption requirements on contractor devices. Create separate access tiers—external users might stream video previews but cannot download master files without additional approval workflows.
Risk-based authentication adapts to user types automatically. Internal employees get streamlined access, while external users face stricter verification requirements that match their limited asset needs.
Network segmentation transforms how dam security zero-trust implementations protect digital assets at the infrastructure level. Software-defined perimeters (SDP) create dynamic security boundaries around DAM components, moving beyond static firewall rules to establish encrypted micro-tunnels for each connection.
Enterprise DAM systems require granular network isolation. High-value brand assets sit in dedicated VLANs with restricted access, while general marketing materials operate in separate network segments. This classification-based approach ensures that a compromise in one asset tier can't cascade across your entire digital library.
Modern ZTNA implementation inspects east-west traffic between DAM components—something traditional perimeter security missed entirely. When your transcoding servers communicate with storage arrays, zero-trust architecture validates every packet exchange, not just initial connections.
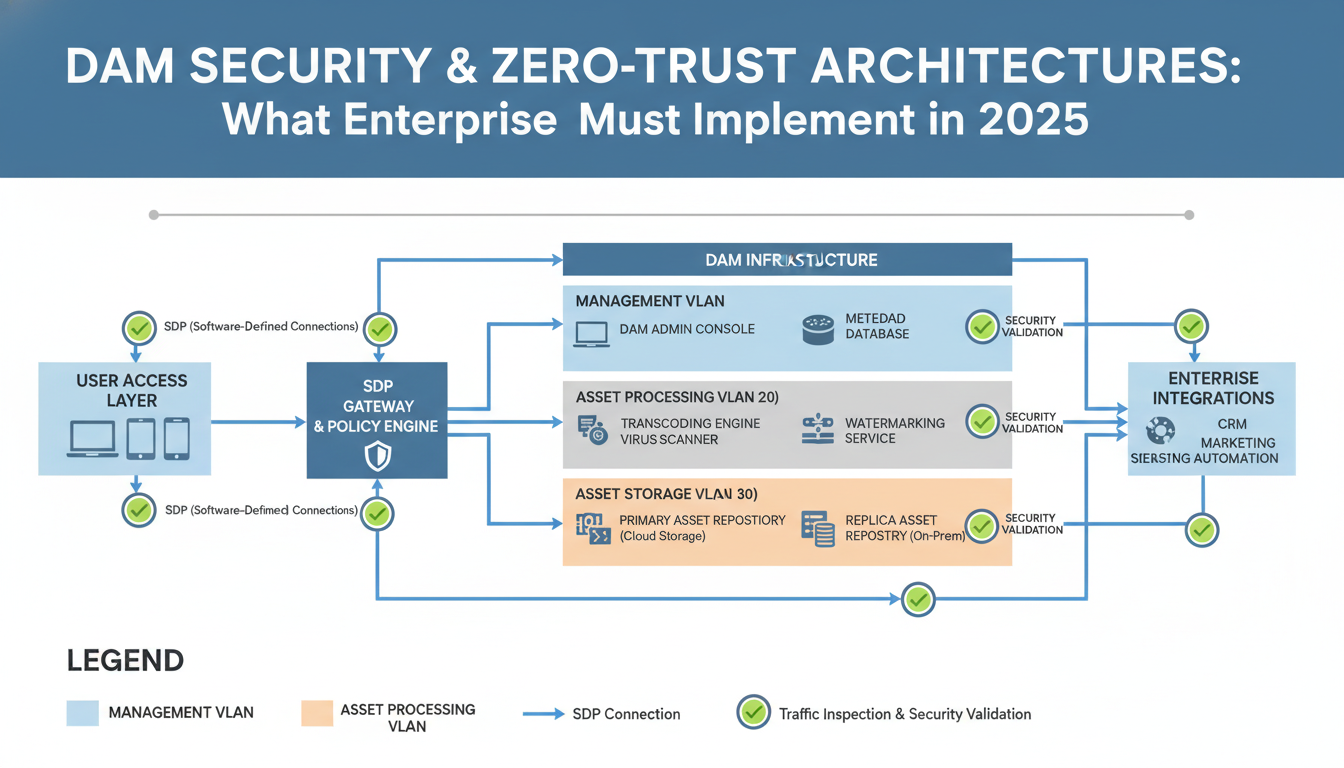
AWS Security Groups, Azure Network Security Groups, and GCP VPC firewall rules enable native segmentation without third-party overlays. However, access policies enforcement adds 8-12ms latency per hop—acceptable for most DAM workflows but critical for real-time video processing.
Pro tip: Configure security group rules to allow direct communication between frequently-accessed DAM components within the same availability zone. This reduces inspection overhead while maintaining asset encryption requirements.
The key challenge? Balancing security granularity with operational complexity. Too many micro-segments create management overhead; too few compromise secure delivery principles.
Cloud-native solutions offer automatic scaling advantages. When your DAM system spins up additional transcoding instances during peak usage, security policies apply automatically without manual VLAN configuration. This automation becomes essential as digital asset volumes grow beyond manual management capacity.
Network segmentation isn't just security theater—it's infrastructure-level dam security zero-trust enforcement that adapts to modern cloud architectures.
dam security zero-trust implementations require continuous monitoring that goes beyond basic access logs. SIEM integration creates the foundation for comprehensive threat detection across your digital asset infrastructure.
Modern enterprises connect DAM platforms with SIEM solutions like Splunk, IBM QRadar, and Microsoft Sentinel to centralize security monitoring. These integrations capture granular DAM events: file access requests, download attempts, permission changes, and asset encryption key rotations.
Splunk's Machine Learning Toolkit processes DAM logs to identify patterns indicating potential threats. A financial services company using this setup detected 847 suspicious download attempts in Q3 2024, preventing potential data exfiltration.
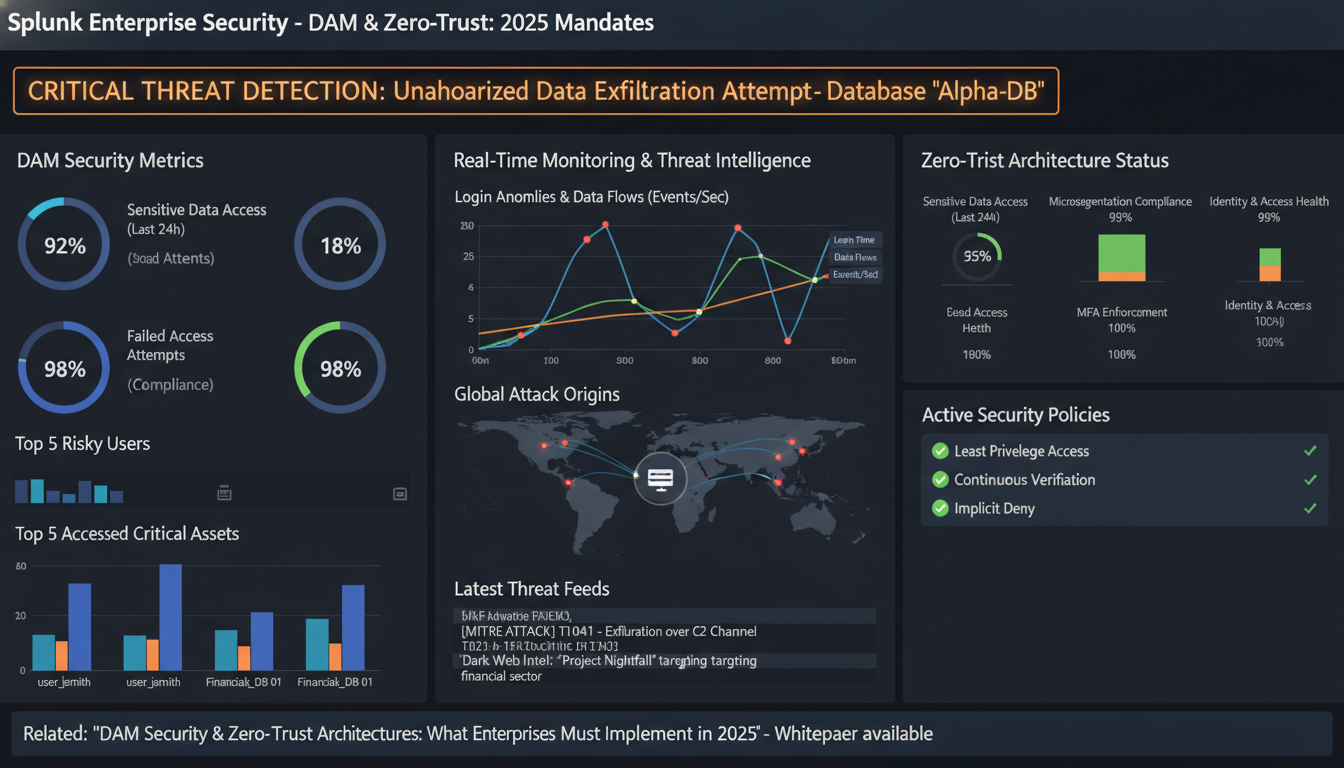
zero-trust architecture monitoring focuses on user behavior deviations. Key metrics include:
Modern DAM systems implement automated responses when threats are detected. Account lockdown occurs automatically after 5 failed authentication attempts. Asset encryption keys rotate immediately when suspicious activity affects high-value content.
Access policies trigger asset quarantine when behavioral analytics detect anomalies. A media company's DAM system automatically quarantined 2,400 video assets when detecting unusual bulk download patterns, preventing intellectual property theft.
Automated reporting satisfies SOX, GDPR, and HIPAA requirements without manual intervention. Secure delivery logs generate compliance reports showing who accessed what assets, when, and from which locations. This automation reduces compliance preparation from weeks to hours while maintaining audit trail integrity.
dam security zero-trust architectures demand seamless integration across your existing security stack. Most enterprises underestimate the complexity of connecting DAM systems with their current infrastructure—a mistake that costs time and budget overruns.
CASB integration creates the first critical connection point. Your Cloud Access Security Broker must monitor every asset encryption event and access policies enforcement. Microsoft Defender for Cloud Apps, for example, can track when users access encrypted assets through your DAM, providing real-time visibility into shadow IT usage patterns.
EDR connectivity amplifies threat detection capabilities. When CrowdStrike or SentinelOne detects suspicious endpoint behavior, your zero-trust architecture should automatically restrict DAM access from that device. This prevents compromised endpoints from accessing sensitive digital assets.
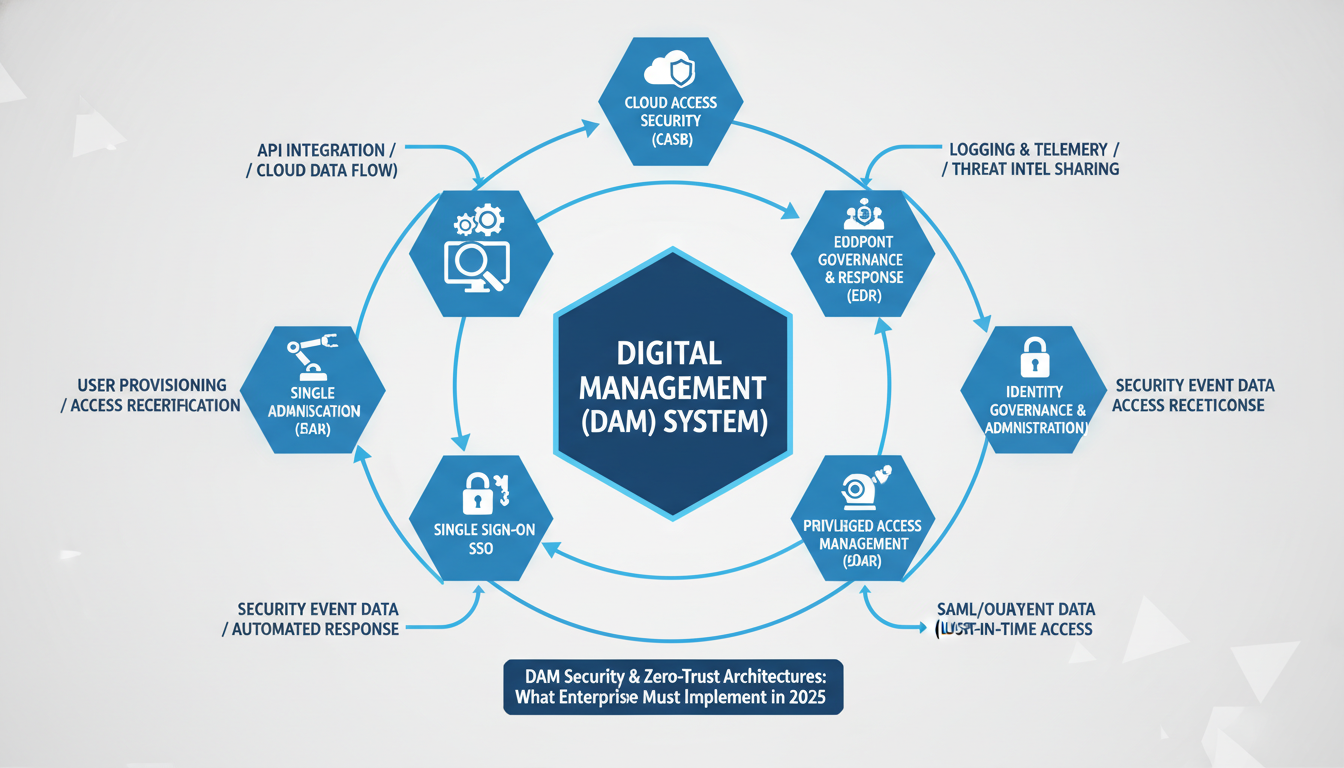
Identity governance platforms like SailPoint or Okta Identity Governance ensure access policies remain current. When employees change roles, IGA systems should trigger automatic DAM permission updates within minutes, not days.
SOAR workflows automate incident response. If your Phantom or Demisto platform detects unauthorized asset downloads, it can immediately revoke access tokens and quarantine affected files. This automation reduces response time from hours to seconds.
SSO and PAM integration completes the security perimeter. Users authenticate once through Ping Identity or Auth0, while CyberArk manages privileged accounts accessing administrative DAM functions. This eliminates password fatigue while maintaining secure delivery protocols.
Budget accordingly—most enterprises allocate $50,000-$200,000 for comprehensive integration projects. This includes API development, middleware licensing, and security testing across all connection points. The investment pays dividends through reduced manual oversight and faster threat response.
Dam security zero-trust implementations must address stringent regulatory requirements that vary significantly across industries. GDPR Article 32 mandates specific technical measures for asset protection, requiring encryption both at rest and in transit. Most enterprises overlook that this applies to every creative file containing personal data—from customer testimonials to employee photos in marketing materials.
SOX Section 404 creates additional complexity for publicly traded companies. Your zero-trust architecture must maintain detailed audit trails for any digital assets used in financial reporting. This includes quarterly report graphics, investor presentation templates, and branded financial documents. The SEC expects automated compliance reporting that tracks who accessed what assets and when.
Healthcare organizations face the strictest requirements under HIPAA's Security Rule. Patient images in marketing campaigns, even anonymized ones, require access policies that limit viewing to authorized personnel only. Asset encryption becomes non-negotiable—a single breach can cost $10.9 million according to IBM's 2023 data breach report.
PCI DSS Level 1 compliance affects retailers more than they realize. Credit card logos, payment interface mockups, and checkout flow designs all contain cardholder data elements. Your secure delivery system must treat these assets with the same protection level as actual transaction data.
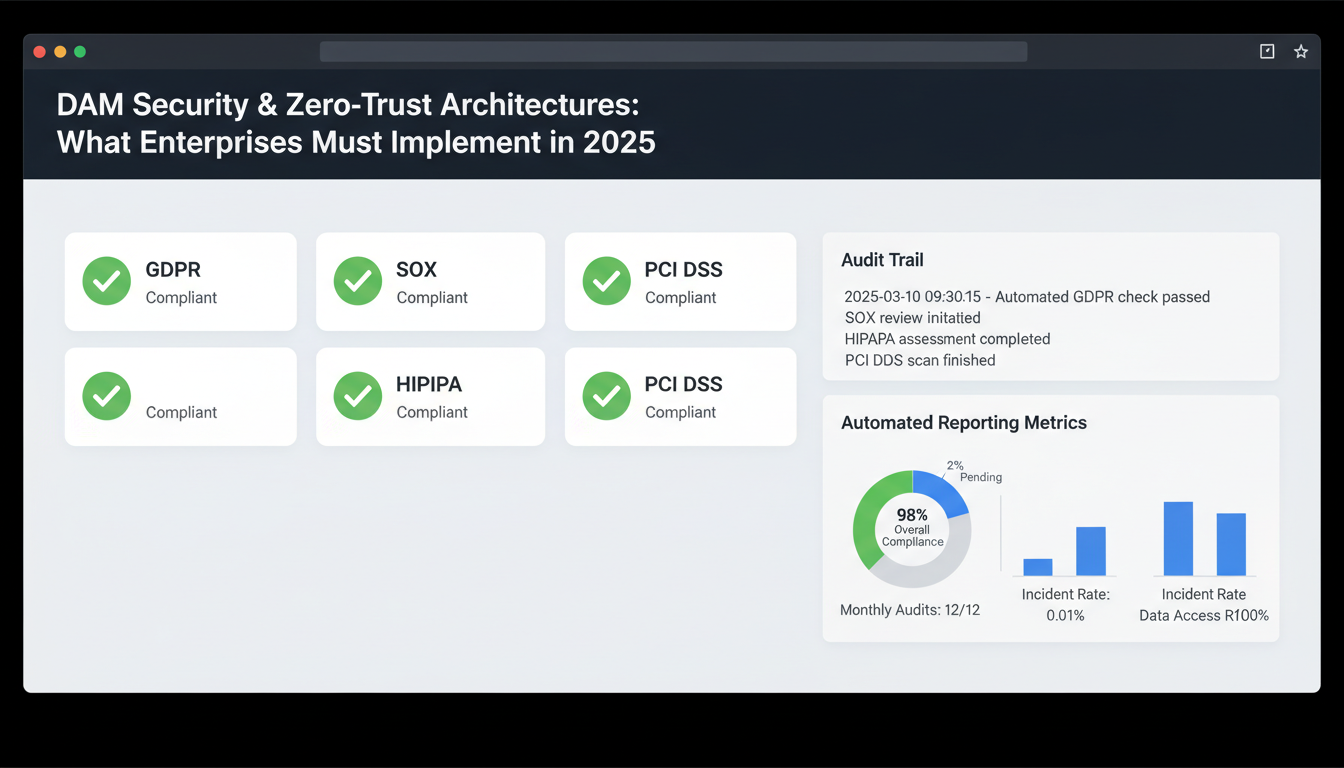
Financial services face additional scrutiny from FINRA and SEC regulations. Investment firm presentations, trading platform screenshots, and client portfolio visualizations require granular permission controls. You can't simply grant marketing teams blanket access to financial assets.
The key insight: compliance isn't just about meeting minimum standards. Smart enterprises use regulatory requirements as the foundation for their dam security zero-trust strategy, building systems that exceed baseline requirements while streamlining audit processes through automated documentation and real-time monitoring.
Dam security zero-trust deployments require careful phasing to minimize disruption while maximizing security gains. Most organizations rush implementation and face costly rollbacks.
Start with comprehensive asset inventory and risk assessment. You'll need one senior security engineer dedicated full-time to catalog existing digital assets, map current access patterns, and identify critical vulnerabilities. Budget $50K-$75K for security auditing tools like Varonis or Microsoft Purview.
Document every integration point. Your DAM system connects to creative tools, CDNs, marketing platforms, and external vendors. Missing even one connection creates security gaps that attackers exploit.
Deploy zero-trust architecture components starting with identity verification and asset encryption. This phase demands 2-3 FTE security engineers plus vendor support contracts ($100K-$300K depending on organization size).
Run pilot programs with 50-100 users maximum. Test access policies under real workloads before expanding. Monitor response times obsessively - users abandon systems that slow their workflow.
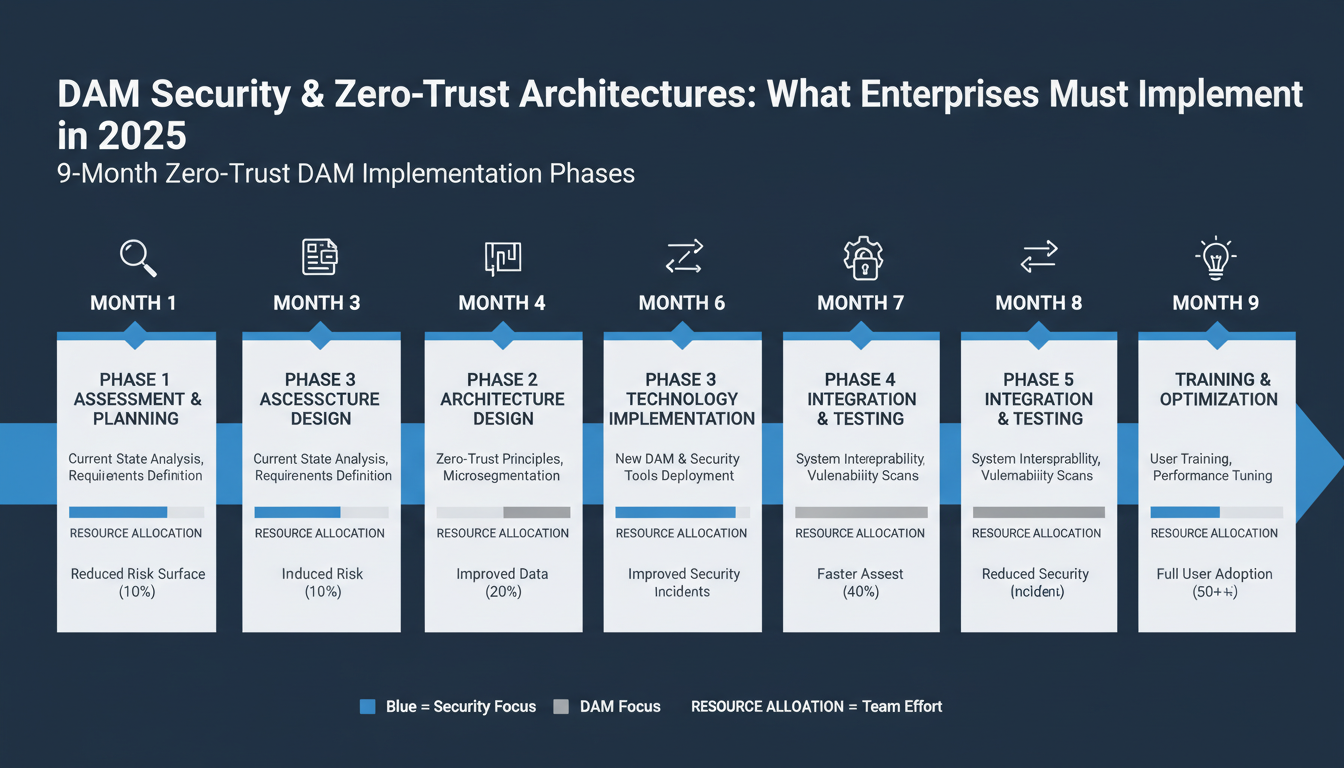
Scale secure delivery mechanisms across all user groups. Train department heads first - they become your change management advocates. Create role-specific training materials rather than generic security presentations.
Track these metrics religiously:
Your RFP must address API compatibility, encryption standards (AES-256 minimum), and compliance certifications. Don't accept vague security promises. Demand specific technical documentation and reference customers in your industry.
Budget $150K minimum for mid-size enterprises, scaling to $500K+ for complex multi-national deployments.
Organizations considering dam security zero-trust architectures face common concerns about costs, performance, and integration complexity. Here's what enterprise leaders need to know.
Most enterprises see positive ROI within 18-24 months of zero-trust architecture deployment. A Fortune 500 media company reduced security incidents by 73% while cutting compliance audit costs from $2.8M to $800K annually. However, initial asset encryption and policy setup can slow file access by 200-300ms per request during the first quarter.
Legacy DAM systems can support zero-trust principles, but require middleware solutions. Adobe Experience Manager customers often deploy identity brokers like Okta or Ping Identity to bridge authentication gaps without full system replacement.
Zero-trust architecture differs from traditional DLP by verifying every access request rather than just monitoring data movement. This means your creative teams using Photoshop or Premiere Pro will authenticate more frequently – typically every 4-6 hours instead of once daily.
Emergency access requires pre-configured break-glass procedures. Smart organizations create time-limited override tokens that automatically expire and trigger security reviews. One healthcare client uses biometric authentication plus manager approval for urgent asset access outside business hours.
Small businesses (under 500 assets) can implement basic zero-trust DAM for $15K-25K annually using cloud-native solutions. Enterprise deployments typically cost $150K-400K in year one, including consulting and integration work.
The biggest workflow disruption? Secure delivery protocols that require recipient verification. Marketing teams report 40% longer campaign approval cycles initially, but most adapt within 90 days as access policies become routine.
Creative software integration remains the trickiest aspect – Adobe CC plugins often need custom development to maintain seamless zero-trust authentication.
The evidence is clear: dam security zero-trust architectures aren't optional for 2025. They're essential survival tools in a threat landscape where traditional perimeter defenses fail daily. Organizations that delay implementation risk becoming the next breach headline.
Two elements can't be compromised: asset-level encryption and granular access policies. Every digital asset needs encryption at rest, in transit, and during processing. Your access policies must verify every user, device, and request—even internal ones. Half-measures create vulnerability gaps that attackers exploit.
The momentum is building fast. Recent surveys show 73% of enterprises plan zero-trust implementation within 12 months. Early adopters gain competitive advantages through reduced breach risks and improved compliance posture. Late adopters face mounting pressure from boards, customers, and regulators.
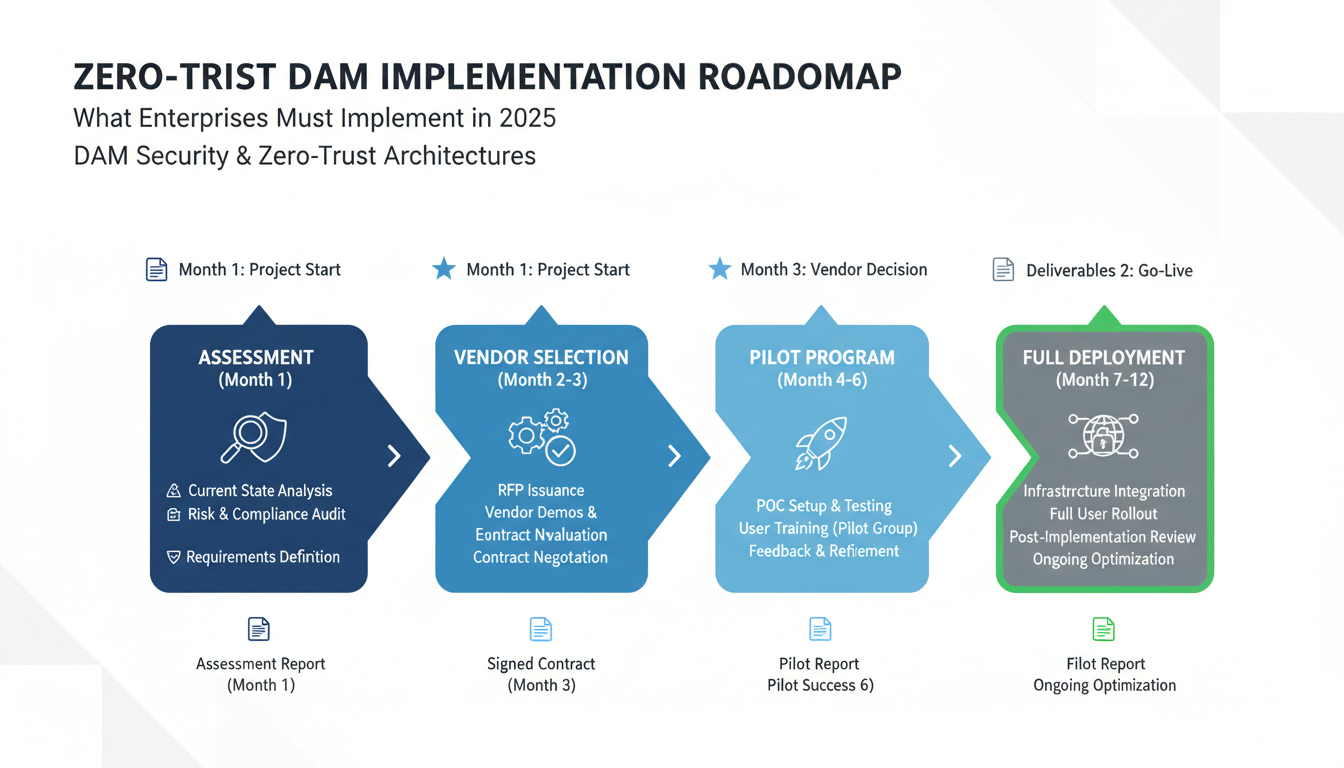
Start with a comprehensive security assessment. Document current DAM vulnerabilities, access patterns, and encryption gaps. This baseline drives vendor evaluation criteria and budget planning.
Evaluate vendors carefully. Request proof-of-concept deployments with your actual assets. Test performance under realistic loads. Verify integration capabilities with existing systems.
Plan your pilot program strategically. Choose a contained asset group—maybe marketing materials or training videos. Measure security improvements and user experience impacts. Use pilot results to refine your full deployment strategy.
Zero-trust architecture represents the future of DAM security. Organizations implementing these frameworks now position themselves ahead of evolving threats and compliance requirements.
Ready to assess your current DAM security posture? Download our comprehensive security assessment checklist or schedule a consultation with our zero-trust specialists. Your digital assets deserve enterprise-grade protection.